Know Your Customer (KYC) is no longer a mere compliance checkbox – it’s a strategic imperative that determines whether financial institutions can scale safely or collapse under regulatory pressure. This comprehensive guide covers everything from foundational principles to cutting-edge implementation strategies, helping you navigate the complexity of KYC compliance in 2025 and beyond.
Whether you’re a fintech founder, compliance officer, or enterprise financial services leader, this guide provides the tactical knowledge to build a KYC program that reduces fraud, passes audits, and accelerates customer onboarding.
What Is KYC (Know Your Customer)? Definition & Purpose
Know Your Customer (KYC) is a foundational compliance framework that requires financial institutions to identify, verify, and understand the customers they serve. More than a regulatory requirement, KYC is your institution’s first line of defense against financial crime, money laundering, terrorist financing, and fraud.
The Three Core Objectives of KYC
- Identity Verification – Confirm that customers are who they claim to be through government-issued identification and supporting documents.
- Risk Assessment – Evaluate each customer’s risk profile based on factors like geography, business type, transaction patterns, and beneficial ownership.
- Ongoing Monitoring – Continuously track customer activity post-onboarding to detect and report suspicious patterns in real time.
KYC is deeply intertwined with Anti-Money Laundering (AML) compliance, though the two serve distinct purposes. While KYC focuses on identity and risk assessment during onboarding, AML encompasses the broader framework of detecting, preventing, and reporting financial crimes throughout the customer lifecycle.
Why KYC Compliance Matters
The stakes are higher than ever. In 2025, regulators worldwide are tightening enforcement, and penalties for non-compliance have reached unprecedented levels. Financial institutions face:
- Multi-million-dollar fines for inadequate KYC programs (EU fintechs have faced penalties exceeding €50 million)
- Criminal liability for executives who fail to implement robust compliance frameworks
- Reputational damage that can erode customer trust and market position in days
- Operational disruption from regulatory investigations and remediation efforts
- Business loss from account closures and customer abandonment during slow onboarding
The Relationship Between KYC and AML Compliance
KYC and AML are complementary but distinct. Think of KYC as the foundation; AML is the structure built on top.
| Aspect | KYC | AML |
|---|---|---|
| Primary Focus | Customer identification & risk profiling | Detecting suspicious financial activity |
| Timeline | Initial onboarding + periodic updates | Ongoing throughout customer lifetime |
| Key Activity | Document verification, beneficial ownership identification | Transaction monitoring, SAR reporting |
| Regulatory Driver | FinCEN (US), FATF, regional regulators | FATF, AML Act, regional frameworks |
| Success Metric | Accurate customer profiles, low false positives | Detection of actual money laundering, SAR quality |
AML requires robust KYC data to function effectively. If your KYC process produces incomplete, inconsistent, or unreliable customer records, your AML transaction monitoring will drown in false positives and miss genuine threats.
The 5 Essential Steps of KYC/AML Onboarding Process
Step 1: Customer Identification Program (CIP)
CIP is the foundation of KYC. It requires you to collect, verify, and maintain accurate customer identification information.
What to collect during CIP:
For individuals:
- Full legal name and any aliases
- Date of birth
- Government-issued ID number (passport, driver’s license, national ID)
- Residential address (with proof of residence no older than 3 months)
- Phone number and email
- Tax identification number (SSN, TIN, or equivalent)
For businesses:
- Legal business name and registered address
- Business registration number (CRN)
- Corporate documents (articles of incorporation, bylaws, memorandum)
- Identification of beneficial owners (individuals holding 20%+ ownership)
- Details of senior management and directors
CIP Verification Methods:
- Document verification – Automated OCR and AI-powered tools to validate government-issued IDs
- Liveness detection – Video selfie with facial recognition to confirm applicant is present
- Database screening – Cross-referencing against government records and reliable third-party data sources
- Multi-factor authentication – Confirming identity through multiple independent data points
Pro Tip: Implement risk-adjusted CIP procedures. New York residents may require different verification than customers from high-risk jurisdictions. Automate routine verifications for low-risk customers, but apply enhanced scrutiny to higher-risk profiles.
Step 2: Customer Due Diligence (CDD)
Customer Due Diligence goes beyond identity verification – it’s about understanding your customer’s financial profile, business operations, and risk characteristics.
CDD requires you to:
- Verify beneficial ownership – Identify all individuals who ultimately own or control 20% or more of the business, particularly for corporate clients
- Understand the nature of the business relationship – What products will they use? What transaction volumes do you expect? What’s their intended use case?
- Assess customer risk profile – Assign a risk rating (low, medium, high) based on geography, industry, business structure, and transaction patterns
- Screen against watchlists – Check customers against sanctions lists (OFAC, UNSC), PEP (Politically Exposed Persons) databases, and adverse media sources
- Document findings – Maintain detailed records of CDD procedures and conclusions for audit purposes
Three Levels of CDD:
Simplified Due Diligence (SDD)
- Applied to low-risk customers (retail consumers, established businesses in low-risk jurisdictions)
- Basic verification and standard monitoring
- Faster onboarding (hours to days)
- Lower per-customer compliance cost
Standard Due Diligence (SDD)
- The baseline for most customers
- Standard document collection, sanctions screening, basic risk assessment
- Ongoing transaction monitoring at standard thresholds
- Typical onboarding: 1-2 hours for automated verification
Enhanced Due Diligence (EDD)
- Reserved for high-risk customers
- Deep investigation into beneficial ownership, sources of wealth, and business legitimacy
- More frequent and intensive transaction monitoring
- May include site visits, third-party audits, or legal verification
- Longer onboarding (2-5 business days)
Step 3: Enhanced Due Diligence (EDD) for High-Risk Customers
Enhanced Due Diligence is triggered when CDD uncovers red flags suggesting elevated risk. EDD requires senior management approval and substantially more investigation.
Triggers for EDD:
- Politically Exposed Persons (PEPs) – Government officials, military leaders, senior judges, or their family members
- Customers from high-risk jurisdictions – FATF gray-list countries, sanctions-listed regions, or jurisdictions with weak AML controls
- Complex ownership structures – Multiple shell companies, trusts, or opaque beneficial ownership
- High-volume or unusual transactions – Rapid movement of large sums, layering patterns, or transactions inconsistent with stated business
- Cash-intensive businesses – Casinos, money changers, precious metals dealers (inherent risk sectors)
- High-net-worth individuals – Wealth concentration justifies deeper scrutiny
- Adverse media – News reports of fraud, corruption, sanctions violations, or financial crime
- Sectors of concern – Cryptocurrency exchanges, trade-based money laundering, offshore financial services
EDD investigative steps:
- Conduct comprehensive background checks on beneficial owners (media reviews, court records, regulatory databases)
- Verify source of funds and source of wealth documentation
- Request additional corporate documents (board resolutions, shareholder registers, ultimate beneficial ownership declarations)
- Review detailed transaction history and business correspondence
- Obtain certifications or third-party verification of business legitimacy
- Potentially conduct site visits for large corporate clients
- Document the EDD conclusion and obtain senior management sign-off
Step 4: Continuous Monitoring (Perpetual KYC)
Continuous monitoring doesn’t end after account opening – it’s the ongoing surveillance and re-verification of customers throughout their lifecycle.
Perpetual KYC includes:
- Transaction monitoring – Analyzing customer transaction patterns in real time to identify deviations from expected behavior
- Periodic customer reviews – Annually or when risk profile changes, re-verify customer information and reassess risk
- Adverse media screening – Continuous monitoring of public sources for negative news or sanctions listings affecting existing customers
- Behavioral analytics – Flagging unusual activity (sudden surge in transaction volume, new beneficiary types, geographic shifts)
- Red flag monitoring – Automated alerts for suspicious patterns: structuring, round-tripping, unusual wire destinations
Adaptive Risk-Based Monitoring:
Modern compliance programs employ dynamic risk assessment. Instead of treating all customers identically, continuous monitoring adjusts thresholds based on customer profile:
- Low-risk customers – Automated monitoring with high alert thresholds; manual review only if significant deviations occur
- Medium-risk customers – Standard rules-based monitoring with quarterly reviews
- High-risk customers – Enhanced monitoring with lower thresholds, weekly reviews, and AI-powered behavioral analysis
The perpetual KYC challenge: One of the most overlooked aspects of modern compliance is that customers change. A customer who was low-risk five years ago might now own an offshore company, relocate to a high-risk jurisdiction, or begin receiving suspicious wire transfers. Effective programs re-evaluate customer risk at least annually and immediately when red flags emerge.
Step 5: Record Keeping & Compliance Reporting
Comprehensive record-keeping is not optional – it’s mandated by law and essential for surviving regulatory audits.
What to maintain:
- Customer identification records – All documents collected during CIP and updates
- CDD/EDD documentation – Complete records of due diligence procedures, findings, and risk assessments
- Beneficial ownership information – Detailed documentation of ultimate beneficial owners
- Sanctions screening results – Proof of screening against OFAC, UNSC, and PEP lists with dates and results
- Transaction records – Complete details of transactions for audit trail purposes
- Monitoring and alert documentation – Records of how alerts were investigated and resolved
- AML policy documentation – Your AML policies, procedures, staff training records, and independent audit results
- SAR/STR filings – Records of Suspicious Activity Reports (SAR) or Suspicious Transaction Reports (STR) submitted to regulators
Record retention requirements:
- Minimum 5-7 years depending on jurisdiction (some require 10+ years)
- Records must be easily retrievable for regulatory review
- Secure storage with access controls and audit trails
- Protection against tampering or unauthorized modification
Compliance Reporting Requirements:
Different jurisdictions require different filings:
- USA: Suspicious Activity Reports (SARs) to FinCEN within 30 days
- EU: Suspicious Transaction Reports (STRs) to national FIUs within specific timeframes
- UK: Disclosures to the National Crime Agency (NCA)
- APAC: Reports to local Financial Intelligence Units
Global KYC Regulations & Standards
KYC requirements are not universal – they’re shaped by international standards and national law. Understanding the global landscape is critical for institutions operating across borders.
FATF Recommendations: The Global Standard
The Financial Action Task Force (FATF) sets the international standard for AML and CFT (Counter-Terrorism Financing) compliance. FATF’s 40 Recommendations form the basis for most national KYC/AML laws.
Key FATF KYC Principles:
- Risk-based approach – Compliance measures should be proportionate to risk (FATF Recommendation 1)
- Customer identification and verification – Mandatory for all customers before establishing relationships (FATF R. 10)
- Enhanced due diligence for high-risk customers – PEPs, high-risk jurisdictions, complex structures (FATF R. 12)
- Ongoing monitoring and transaction reporting – Continuous surveillance and timely STR/SAR reporting (FATF R. 16)
- Record-keeping – Maintain KYC records and transaction details for minimum 5 years (FATF R. 11)
2025 FATF Update: Recent FATF amendments (June 2025) emphasize:
- Stricter Ultimate Beneficial Ownership (UBO) disclosure requirements
- Greater transparency in cross-border transactions
- Accountability for AI-driven compliance decisions
- Real-time monitoring expectations
United States: The Bank Secrecy Act (BSA) & FinCEN Framework
The Bank Secrecy Act, administered by FinCEN (Financial Crimes Enforcement Network), is the primary US framework.
US KYC Requirements:
- Customer Identification Program (CIP) – Verify name, DOB, address, and ID (OFAC-compliant)
- Customer Due Diligence (CDD) – Added in 2016; requires understanding beneficial ownership, nature of business, and risk assessment
- Sanctions Screening – Check against Office of Foreign Assets Control (OFAC) lists before account opening
- SAR Filing – Report suspicious transactions to FinCEN within 30 days
- CTR Filing – Currency Transaction Reports for cash transactions over $10,000
2025 US Trends:
- Increased scrutiny of crypto exchanges and digital asset service providers (VASPs)
- Beneficial Ownership Registry (CTA) requiring corporate transparency
- Real-time payment infrastructure (FedNow) creating new AML compliance demands
- Stronger enforcement against “shadow banking” and straw purchases
European Union: The AML Directives
The Anti-Money Laundering Directive (AMLD5, implemented December 2020, with AMLD6 forthcoming) harmonizes KYC across EU member states.
EU KYC Mandate:
- Strict customer identification and beneficial ownership verification
- Enhanced due diligence for high-risk customers and PEPs
- PEP registry requirements (some member states)
- Mandatory reporting of suspicious transactions to national FIUs
- 5-year record retention (minimum)
- Strong penalties for non-compliance (up to €50 million or 10% of annual revenue)
GDPR Intersection: EU KYC must comply with GDPR data protection rules. This creates tension: you must collect comprehensive customer data for compliance, but GDPR restricts how you store, use, and retain it. The solution: implement privacy-by-design, use consent management tools, and maintain clear data retention schedules.
United Kingdom: Post-Brexit Framework
Post-GDPR/post-Brexit, the UK has established its own regulatory framework under the FCA (Financial Conduct Authority).
UK Requirements:
- Aligned with FATF standards and AMLD
- PEP screening mandatory
- Sanctions list checks (UK Sanctions List, plus UNSC/EU lists)
- Risk-based approach to due diligence
- Enhanced scrutiny for high-risk customers and high-risk jurisdictions
Asia-Pacific: Varying Standards
Singapore (MAS Notice 626):
- Strict KYC aligned with FATF
- Real-time transaction monitoring
- Immediate SAR reporting for suspicious activity
- Enhanced controls for crypto and digital asset firms
Hong Kong (AMLO):
- Rigorous customer due diligence
- Beneficial ownership verification
- Continuous monitoring and suspicious transaction reporting
- Penalties up to HKD 3 million for individuals, HKD 5 million for companies
Australia (AML/CTF Act):
- Risk-based compliance approach
- Customer identification and verification (CIV)
- Beneficial ownership reporting
- Transaction reporting (AUSTRAC)
Latin America & Middle East
LATAM regulatory environment:
- Variable standards across countries (Mexico, Brazil, Argentina have strict regimes)
- Many jurisdictions adopt FATF Recommendations but with enforcement gaps
- Growing focus on crypto and cross-border transaction monitoring
MENA region:
- Heavy emphasis on sanctions compliance (especially for US/UN-listed entities)
- Strict OFAC screening requirements
- Strong AML frameworks in mature financial centers (UAE, Saudi Arabia)
KYC Due Diligence Process: Explained Step-by-Step
Understanding the tactical flow of a complete KYC due diligence process helps you design better workflows and identify bottlenecks.
The Complete KYC Process Flow
Phase 1: Initial Data Collection
- Customer provides basic information (name, address, DOB, ID)
- Document upload: government-issued ID, proof of address
- For businesses: corporate documents, shareholder information
Phase 2: Identity Verification
- OCR scanning and AI-powered document validation
- Liveness detection and facial recognition
- Cross-referencing against government databases and reliable sources
- Biometric checks (fingerprint, iris scanning in some jurisdictions)
Phase 3: Risk Assessment
- Profile analysis: geography, business type, transaction patterns, industry
- Sanctions and PEP screening
- Adverse media review
- Risk score calculation (low/medium/high)
Phase 4: Due Diligence Level Assignment
- SDD: Low-risk profiles proceed to account opening
- Standard CDD: Medium-risk profiles receive standard monitoring
- EDD: High-risk customers flagged for enhanced investigation
Phase 5: EDD (If Required)
- Senior management review
- Beneficial ownership deep dive
- Source of funds verification
- Enhanced background checks
- Decision: approve, conditional approval, or decline
Phase 6: Account Opening & Enrollment
- Final compliance check
- Approved customers activated in system
- Initial KYC record documented
Phase 7: Ongoing Monitoring
- Continuous transaction monitoring
- Periodic customer reviews (annual minimum)
- Adverse media screening
- Behavioral analytics and red flag detection
Processing Time Benchmarks
The research shows significant variation:
| Activity | Benchmark | Industry Average | Best Practice |
|---|---|---|---|
| CIP completion | 5-15 minutes | 1-2 hours | 15-30 minutes (automated) |
| CDD screening | 10-30 minutes | 1-2 hours | 20-40 minutes (automated) |
| EDD investigation | 2-8 hours | 2-5 days | 4-12 hours (with good data) |
| Total SDD process | 1-2 hours | varies | 30-60 minutes |
| Total with EDD | 2-5 days | 2-7 days | 4-24 hours |
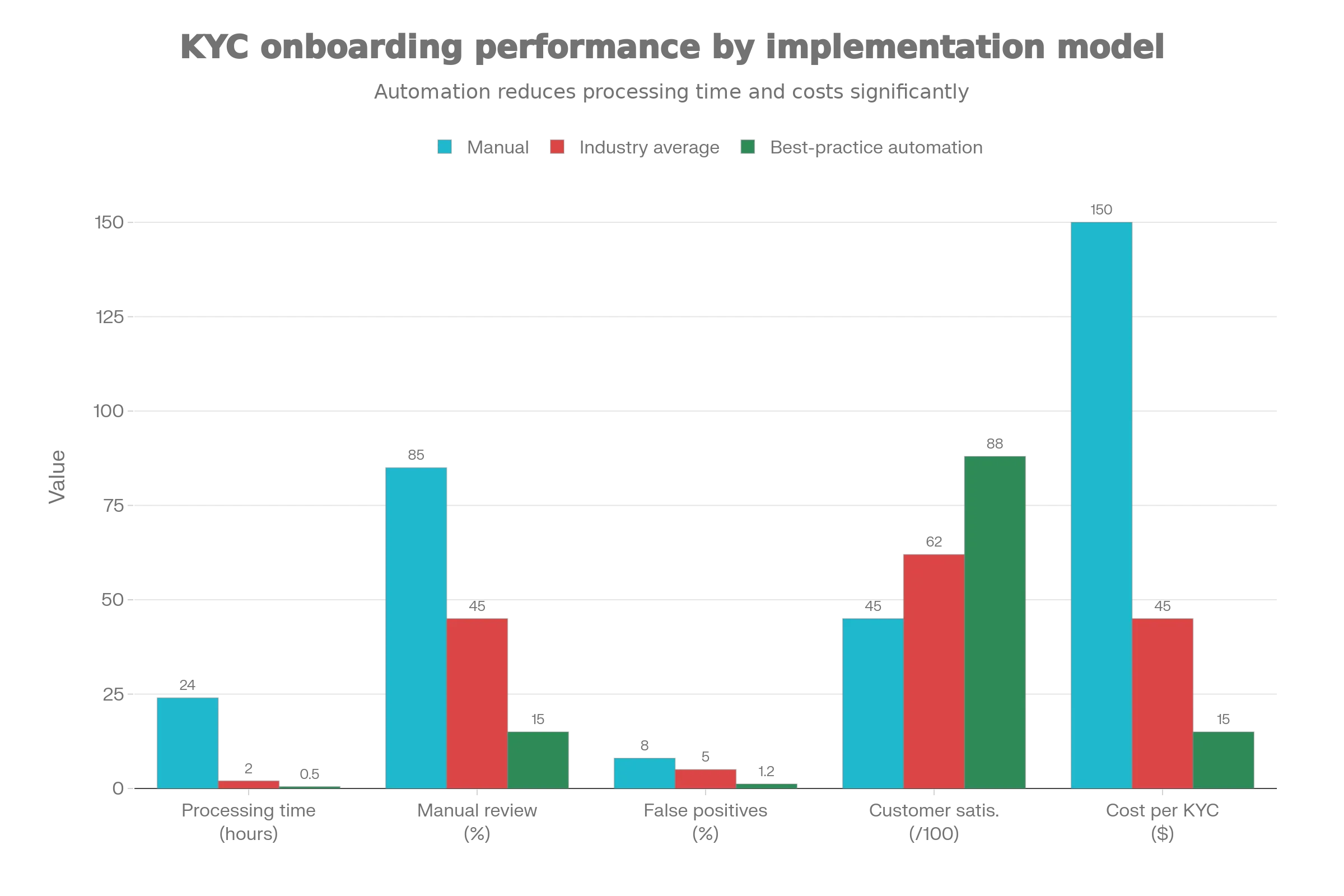
Modern best practice: With proper automation, institutions are achieving 80% reduction in processing time compared to fully manual processes. What once took 1-2 weeks now takes 1-2 hours for straightforward cases.
KYC Best Practices: Building a Robust Compliance Program
1. Adopt a Risk-Based Approach
The one-size-fits-all model is dead. Effective KYC programs allocate resources based on actual risk.
Risk-based framework:
- Tier 1 (Low-Risk): Retail consumers, established businesses in low-risk jurisdictions → automated verification, streamlined onboarding
- Tier 2 (Medium-Risk): Small businesses, consumers from moderately-risky jurisdictions → standard CDD, regular monitoring
- Tier 3 (High-Risk): PEPs, large cash businesses, complex structures, sanctioned jurisdictions → EDD, enhanced monitoring, senior management approval
This approach balances compliance rigor with customer experience – good customers get frictionless onboarding, while bad actors face appropriate scrutiny.
2. Implement Centralized Customer Data Management
The silent killer of compliance programs is data fragmentation. When customer information lives in silos (onboarding system, lending platform, fraud detection tool, transaction monitoring), you create inconsistency, duplication, and blind spots.
Solution: Build a single customer record that’s accessible across your compliance ecosystem:
- Unified customer profile with all verification and due diligence findings
- Real-time synchronization across systems
- Version control and audit trails for all updates
- Exception handling for inconsistencies between systems
3. Leverage Advanced Technology for Automation
Manual KYC is the enemy of scale. Every document manually reviewed, every sanctions list manually checked, every customer profile manually assessed is a bottleneck.
Technology priorities:
- Automated ID verification – OCR + AI-powered document authenticity checks (reduces manual review by 70-80%)
- Biometric authentication – Liveness detection, facial recognition, fingerprint matching (eliminates fraud from stolen credentials)
- Sanctions and PEP screening – Automated, real-time checks against 200+ global databases with fuzzy matching to handle name variations
- Adverse media scanning – AI parsing of news sources and public databases to flag new information about existing customers
- Transaction monitoring – Machine learning models to identify suspicious patterns without drowning analysts in false alerts
- Risk scoring engines – Automated risk assessment based on 100+ signals (geography, industry, behavior, transaction patterns)
The ROI on automation is staggering: Financial institutions report 5-6x faster onboarding with automation while reducing manual effort by 60-80% and achieving lower false positive rates through smarter algorithms.
4. Implement Multi-Factor Verification
Never rely on a single data point. Effective KYC uses multiple independent verification sources:
- Government ID verification (primary)
- Database cross-reference (secondary)
- Address verification (tertiary)
- Biometric confirmation (quaternary)
- Third-party verification (when appropriate)
This defense-in-depth approach catches fraud vectors that single-factor systems miss.
5. Create Clear Escalation Workflows for Edge Cases
Not all decisions are binary. A customer might have a legitimate reason for residing in a high-risk jurisdiction, or have a name match on a sanctions list that’s clearly not the same person (false positive).
Best practice:
- Define clear criteria for escalation to senior compliance officer
- Establish timeframes for decision (e.g., 24 hours for medium-risk edge cases)
- Document the decision and reasoning for audit purposes
- Build feedback loops so edge cases inform system tuning
6. Maintain Audit-Ready Documentation
Regulatory audits are a when, not an if. Your entire KYC program must be defensible.
Documentation to maintain:
- KYC policy and procedures documentation
- Evidence of customer verification (with timestamps)
- Risk assessment and scoring documentation
- EDD investigation files and decision records
- Training records showing staff compliance awareness
- Independent audit results
- Testing and quality assurance procedures
Pro tip: Use a centralized case management system that automatically generates audit-ready reports and maintains tamper-proof logs.
7. Foster a Compliance Culture
Compliance is not the compliance team’s job – it’s everyone’s.
- Train frontline staff to recognize red flags
- Create reporting mechanisms for suspicious activity
- Reward compliance culture and hold people accountable for violations
- Leadership must visibly prioritize compliance, not view it as a cost center
- Regular communication about regulatory changes and new threats
KYC Challenges, False Positives & Solutions
The False Positive Epidemic
The dirty secret of AML compliance: 90%+ of alerts are false positives. A customer’s name matches a sanctions list entry (it’s a different person). Transaction patterns look suspicious but have innocent explanations. Behavioral changes are legitimate (customer moved, changed jobs, started a new business).
The cost of false positives:
- Operational cost: Financial institutions spend an average of 4 hours investigating each alert; with thousands of false alerts, this translates to hundreds of thousands of wasted analyst hours annually
- Business cost: Legitimate customers who get flagged, delayed, or rejected abandon the platform or switch to competitors
- Regulatory risk: While investigating false positives, real threats slip through; alert backlogs create compliance violations
- Reputational cost: False rejections damage customer relationships and brand trust
One global bank discovered that false positives consumed 95% of its compliance team’s time, leaving just 5% for investigating actual risks.
Solutions to Reduce False Positives
1. Smarter Screening Algorithms
- Use fuzzy matching to account for name variations (transliterations, nicknames, typos)
- Incorporate contextual data (age, date of birth, address) to disambiguate name matches
- Continuous refinement based on investigator feedback
2. Risk-Adjusted Thresholds
- Don’t apply the same alert threshold to all customers
- Low-risk customers: higher thresholds, fewer alerts
- High-risk customers: lower thresholds, more intensive monitoring
- Result: fewer total alerts with higher signal-to-noise ratio
3. AI-Powered Triage
- Machine learning models trained on historical investigation data
- Automatically categorize alerts as high-confidence, medium-confidence, or low-confidence
- Route high-confidence alerts to human analysts; auto-clear low-confidence alerts with documentation
- Result: analysts focus on cases with highest potential risk
4. Behavioral Analytics
- Instead of rule-based monitoring (transaction over $X triggers alert), use behavioral models
- Each customer has a unique profile: typical transaction size, frequency, beneficiary types, time of day
- Deviations from profile trigger investigation
- Learning: algorithm adapts as customer behavior legitimately changes
5. Enhanced Data Quality
- Garbage in, garbage out: high-quality customer data is the foundation
- Standardize data collection and validation
- Regular data quality audits
- Correct inconsistencies before they contaminate alert generation
Balancing Speed & Accuracy
One of the critical trade-offs in KYC is the speed vs. accuracy problem. Faster verification processes (15 minutes) may miss subtle red flags that deeper investigation (2 hours) would catch.
Solution: Use a tiered approach:
- Fast-track path (15-30 min) – Low-risk customers get automated verification, immediate decision
- Standard path (1-2 hours) – Medium-risk customers get standard CDD with manual review
- Deep-dive path (2-5 days) – High-risk customers get EDD with senior management involvement
This achieves both: most customers (80%+) get frictionless fast-track onboarding, while actual risks receive appropriate scrutiny.
Technology & Innovation in KYC
AI and Machine Learning Transformation
AI is reshaping KYC from a manual, reactive process to an automated, predictive system.
AI Applications:
- Identity Verification – Facial recognition accuracy now exceeds 99% in controlled conditions; systems detect deepfakes and spoofing attempts
- Risk Scoring – ML models trained on millions of transactions predict customer risk better than human analysts; continuous learning improves performance
- Transaction Monitoring – Anomaly detection algorithms identify unusual patterns humans might miss; adaptive thresholds reduce false positives
- Document Analysis – OCR + AI extract key information from complex documents, validate authenticity, and flag forgeries
- Adverse Media Screening – NLP parsing of news sources identifies mentions of customers and sanctions listings in real time
2025 Reality Check: AI-powered KYC systems report 97% accuracy on approvals with minimal false accepts, and 80% reduction in processing time compared to manual systems.
Blockchain & Decentralized Identity
Blockchain technology promises to solve a fundamental KYC inefficiency: duplicated verification efforts. When a customer relationships with Bank A undergoes extensive KYC, Bank B can’t reuse that work – they repeat the process from scratch.
Blockchain solution: Decentralized identity (DI) or self-sovereign identity (SSI) creates portable, tamper-proof credentials:
- Customer undergoes KYC once
- Verification result stored on blockchain (immutable, transparent)
- Customer can share verified credentials with multiple institutions
- Each institution validates the credential’s authenticity via blockchain
- Result: customers complete KYC once, not multiple times
Current status (2025): Promising pilot programs, but regulatory uncertainty and implementation complexity slow adoption. Most institutions still rely on traditional verification, though blockchain integration is accelerating in crypto and fintech sectors.
Biometric Authentication
Beyond facial recognition, biometric KYC now includes:
- Fingerprint scanning – High accuracy, spoofing-resistant
- Iris recognition – Extremely accurate, hard to spoof
- Voice recognition – Passive verification during customer service calls
- Behavioral biometrics – Keystroke dynamics, mouse movements, typing patterns create unique user profiles
- Liveness detection – Video selfie combined with micro-expressions and micro-movements to prevent deepfakes
Advantage: Multimodal biometric systems (combining 2-3 biometric factors) achieve near-perfect fraud detection while remaining user-friendly.
Real-Time Compliance Integration
Modern fintech and payments platforms are embedding KYC compliance into the transaction itself:
- Instant KYC on payment flows – Verify beneficiary identity before transfer completes
- Real-time sanctions screening – Check wire destination against sanctions lists before transaction settles
- Behavioral KYC – Monitor transaction patterns in real time and adjust risk profile dynamically
- API-based verification – Integrate identity verification into apps and websites seamlessly
Result: Instead of compliance as a separate, painful process, it becomes invisible infrastructure.
Selecting the Right KYC Software: Features & Evaluation Criteria
If you’re evaluating KYC platforms, focus on these core capabilities:
Essential Features
| Feature | Why It Matters | Red Flag If Missing |
|---|---|---|
| Automated ID Verification | Reduces manual review bottleneck | Only offers manual document review |
| Multi-Channel Screening | OFAC, sanctions, PEP, adverse media integrated | Requires separate third-party vendors |
| Risk-Based Workflows | Different paths for different risk profiles | One-size-fits-all process |
| Real-Time Transaction Monitoring | Catches ongoing suspicious activity | Historical batch processing only |
| Centralized Case Management | Single view of customer across systems | Fragmented, siloed investigations |
| Audit Trail & Reporting | Demonstrates compliance to regulators | Limited logging or manual reporting |
| Scalability & API Access | Grows with your business | Requires manual processes to scale |
| Integration Capabilities | Connects to existing banking systems | Requires manual data entry between systems |
| Customization & Rules Engine | Adapt to your specific risk profiles and jurisdictions | Fixed rule sets, no customization |
Platform Evaluation Framework
- Compliance Coverage – Does it meet requirements in all jurisdictions where you operate? (FATF, OFAC, EU, UK, APAC, etc.)
- Integration Depth – How easily does it connect to your core banking systems, payment processors, fraud tools?
- Automation Level – What percentage of cases can be processed without human intervention?
- False Positive Management – How does it reduce alert noise? What’s the historical false positive rate?
- Performance Metrics – Average processing time, manual review percentage, audit pass rate, customer satisfaction
- Scalability – Can it handle 10x growth without proportional cost increases?
- Support & Expertise – Does the vendor provide implementation support, training, and ongoing compliance consulting?
- Cost Structure – Transparent pricing? Does it scale with transaction volume?
Leading KYC Solutions (2026 Market)
| Platform | Strengths | Best For |
|---|---|---|
| Sumsub | Comprehensive AML/KYC, strong fintech focus, 5-6x faster onboarding | Fintechs, crypto, payments |
| Onfido | ID verification excellence, strong UX, global reach | Consumer onboarding, mass market |
| Trulioo | Global identity verification, 195 countries, emerging market strength | International expansion, APAC |
| ComplyAdvantage | Sanctions & PEP screening leader, real-time database access | Banks, asset managers, high-volume firms |
| Veriff | Video verification, liveness detection, mobile-first | Crypto, fintech, Asia-focused |
| Sanctify | Sanctions specialist, trade-based money laundering focus | Import/export, trade finance |
10-Step Implementation Roadmap for KYC Programs
Whether you’re building from scratch or upgrading an existing program, follow this proven implementation roadmap:
Step 1: Conduct a Gap Analysis & Risk Assessment
- Map current KYC procedures against regulatory requirements in your jurisdictions
- Identify gaps in CIP, CDD, EDD, monitoring, and record-keeping
- Assess your current false positive rate, processing time, and compliance audit results
- Prioritize gaps by risk level
Output: Gap analysis report and remediation roadmap
Step 2: Define KYC Policy & Procedures
- Document your KYC objectives, scope, and risk-based framework
- Define due diligence levels for different customer types and risk profiles
- Establish procedures for CIP, CDD, EDD, monitoring, and reporting
- Create workflows for escalation, exceptions, and manual review
- Document record-keeping and retention requirements
Output: Formal KYC policies and procedures documentation
Step 3: Build Your Risk Framework
- Define risk factors: geography, industry, customer type, transaction size, business structure
- Create risk scoring model (quantitative or qualitative)
- Establish decision rules: risk score → CDD level → due diligence depth
- Test framework against historical customer data
- Refine based on outcomes
Output: Risk framework and scoring matrix
Step 4: Select & Implement Technology
- Evaluate KYC platforms against requirements
- Select platform based on compliance coverage, integration, automation, and cost
- Plan phased implementation (don’t try to migrate everyone at once)
- Build integrations with core banking, payments, fraud systems
- Establish data governance and quality standards
Output: Live KYC platform with integrations to existing systems
Step 5: Train & Certify Your Team
- Develop training program covering:
- Regulatory landscape (FATF, OFAC, GDPR, etc.)
- Company KYC policies and procedures
- Technology platform training
- Red flag recognition
- Escalation protocols
- Record-keeping requirements
- Implement annual recertification
- Conduct specialized training for EDD investigators
Output: Trained, certified compliance team
Step 6: Pilot with Low-Risk Customers
- Start with automated-friendly customer segments
- Test end-to-end workflows before full rollout
- Identify bottlenecks, data quality issues, integration gaps
- Refine procedures based on pilot results
- Build confidence in team and leadership
Output: Validated procedures and trained operations team
Step 7: Execute Full Rollout & Migration
- Migrate existing customers through updated KYC process
- Phase by risk level: low-risk first (less investigation needed), high-risk later
- Monitor processing time, manual review rate, false positive rate during migration
- Maintain legacy process in parallel for contingency
- Celebrate team achievements during rollout
Output: Compliant customer base under new procedures
Step 8: Implement Continuous Monitoring
- Activate transaction monitoring for all customers
- Set thresholds appropriate for each risk profile
- Establish adverse media screening and re-screening cadence
- Define periodic customer review schedule
- Build escalation protocols for monitoring alerts
Output: Automated monitoring dashboard with real-time alerts
Step 9: Conduct Testing & Quality Assurance
- Execute independent audit of KYC processes (internal or external)
- Review sample of customer files for completeness of documentation
- Test alert investigation protocols
- Validate risk scoring accuracy
- Assess SAR/STR quality and timeliness
- Document findings and remediation
Output: Audit report with compliance assessment
Step 10: Establish Continuous Improvement Process
- Monitor key metrics: processing time, false positive rate, audit pass rate, customer satisfaction
- Quarterly reviews of procedures, thresholds, and technology effectiveness
- Feedback loops: investigators → analysts → risk engineers → refinement
- Stay current on regulatory changes
- Annual policy and procedure review
- Regular team meetings to address challenges and share lessons
Output: Self-improving compliance program that adapts to evolving risks and regulations
KYC Compliance Checklist
Use this checklist to audit your KYC program:
Customer Identification Program (CIP)
- Collect full legal name, date of birth, address, government ID, tax ID for all customers
- Verify identity through independent, reliable sources
- Screen all customers against sanctions lists (OFAC, UNSC) before account opening
- Document CIP procedures and evidence in customer file
- Maintain CIP records for minimum 5 years
Customer Due Diligence (CDD)
- Understand nature of customer’s business and expected transaction types
- Assess customer risk profile (low/medium/high)
- Screen against PEP databases and adverse media
- For businesses, identify all beneficial owners (20%+ ownership)
- Document CDD findings and risk assessment
- Assign appropriate due diligence level based on risk
Enhanced Due Diligence (EDD)
- Apply EDD to all high-risk customers (PEPs, high-risk jurisdictions, complex structures)
- Conduct enhanced investigation: background checks, source of funds verification
- Obtain senior management approval for high-risk accounts
- Document EDD procedures and findings comprehensively
- Make clear approval/decline/conditional decision
Ongoing Monitoring
- Monitor all customer transactions for suspicious activity in real time
- Re-verify customer information at least annually
- Screen existing customers against new sanctions and PEP additions
- Monitor adverse media for mentions of customers
- Adjust risk profile if customer behavior or circumstances change
- Maintain monitoring logs and investigation records
Reporting & Record-Keeping
- File Suspicious Activity Reports (SARs) or Suspicious Transaction Reports (STRs) within regulatory timeframes
- Include adequate detail in SAR/STR filings to support investigation
- Maintain all KYC documentation in searchable, secure system
- Retain records for minimum required period (typically 5+ years)
- Ensure records are audit-ready with clear timestamps and decision documentation
Compliance Program
- Document formal KYC policies and procedures
- Appoint AML Compliance Officer responsible for program
- Conduct annual independent audit of KYC program
- Train all relevant staff on KYC requirements annually
- Maintain training documentation and attendance records
- Test and validate systems and procedures regularly
- Update policies promptly when regulations change
Frequently Asked Questions: KYC Compliance
Q: How long does KYC verification typically take?
A: With modern automated systems, 15-30 minutes for simple cases. Standard CDD with verification: 1-2 hours. EDD for high-risk customers: 2-5 business days. Manual, paper-based processes can take 1-3 weeks.
Q: What if a customer is on a sanctions list?
A: You cannot open an account. Immediately block all transactions and file a Specially Designated Nationals (SDN) report with OFAC (US) or equivalent regulator. Consult legal counsel before communicating with the customer (in some cases, communication itself violates sanctions law).
Q: Do I need to re-verify existing customers?
A: Yes. Regular re-verification (typically annually, or when risk profile changes) is required. This is part of “perpetual KYC” or “continuous monitoring.” Additionally, customers should be screened against updated sanctions and PEP lists regularly.
Q: What’s the difference between KYC and background checks?
A: KYC is regulatory compliance focused on identity verification and risk assessment. Background checks are deeper personal/professional history investigations, often used for employment or high-risk customers but not always required by regulation.
Q: Can customers complete KYC remotely?
A: Yes. Remote KYC using video verification, biometrics, and digital document upload is now standard and legally recognized in most jurisdictions. However, some high-risk or high-net-worth customers may require in-person verification.
Q: How do I handle customers from high-risk jurisdictions?
A: Apply Enhanced Due Diligence. This includes deeper background investigation, verification of business legitimacy, possible source of funds documentation, and enhanced monitoring. Many institutions establish risk-based thresholds: some jurisdictions trigger automatic EDD; others are evaluated case-by-case.
Q: What qualifies as a red flag for money laundering?
A: Common red flags include:
- Structuring (multiple transactions just below reporting thresholds)
- High-volume cash transactions inconsistent with stated business
- Round-tripping (money flowing in and out immediately)
- Unusual beneficiary types or frequent destination changes
- Transactions to/from sanctioned jurisdictions
- Politically exposed persons with unexplained wealth
- Customers providing vague information about business purpose
Q: How often should I update my KYC procedures?
A: At minimum, annually. However, updates should be more frequent if:
- Regulatory requirements change (which happens frequently)
- Your independent audit identifies gaps
- You experience false positives or compliance failures
- New threat vectors or fraud patterns emerge
- Your technology platform is upgraded
Q: Can I use a third-party vendor for KYC?
A: Yes, but you remain ultimately responsible. If you outsource KYC to a vendor, you must:
- Conduct due diligence on the vendor
- Monitor their performance and compliance
- Maintain oversight of KYC quality
- Ensure data security and privacy compliance
- Accept regulatory liability for their failures
Q: What happens if I’m found non-compliant with KYC requirements?
A: Consequences escalate based on severity:
- Warning letters and compliance orders from regulators
- Fines (ranging from thousands to tens of millions of dollars)
- Mandatory remediation programs
- Prohibition from onboarding new customers
- Loss of banking licenses or operating permits
- Criminal liability for executives (in severe cases)
The Future of KYC: 2025-2026 & Beyond
Regulatory Trends
Stricter enforcement – Regulators are moving from guidance to enforcement. The days of vague, principles-based compliance are over. Specific requirements are becoming law.
Ultimate Beneficial Ownership (UBO) transparency – Global push toward disclosing who really owns and controls businesses (not just listed directors). This is becoming more important than the company entity itself.
AI accountability – As AI automates compliance decisions, regulators demand “explainability.” You can’t simply say “the algorithm rejected the customer.” You must explain why, with audit trails.
Cross-border standardization – FATF working toward harmonized global standards. Likely outcome: businesses can build one KYC framework instead of 15 different ones per jurisdiction.
Crypto & Digital Assets Integration – Crypto regulation is coalescing around KYC/AML principles. Expect crypto exchange KYC requirements to become as rigorous as traditional banking within 2-3 years.
Technology Evolution
AI-native compliance – Compliance built on machine learning from the ground up, not AI bolted onto legacy systems. Predictive compliance instead of reactive.
Decentralized identity – Blockchain-based reusable identity credentials gaining traction. Customers complete KYC once; institutions trust the credential across platforms.
Continuous, real-time compliance – From annual KYC reviews to continuous identity re-verification and risk assessment. Behavioral biometrics and adaptive monitoring become standard.
Privacy-preserving verification – Techniques like zero-knowledge proofs and homomorphic encryption allow KYC verification without exposing sensitive customer data.
Competitive Differentiation
Speed is a differentiator – Companies that can deliver frictionless 15-minute onboarding while maintaining compliance will win market share. Customers have low tolerance for KYC friction.
Trust is a moat – As regulations tighten, customers increasingly choose platforms they trust to be compliant. A history of zero regulatory incidents becomes a competitive advantage.
Data quality is an asset – Companies building clean, comprehensive customer profiles can leverage that data for better fraud detection, risk management, and customer experience.
Conclusion
Mastering KYC compliance is no longer optional – it’s essential to your institution’s survival and success. The regulatory landscape is tightening, penalties are escalating, and customer expectations for friction-free onboarding are rising. The institutions that master this balance – compliance rigor combined with user experience excellence – will dominate.
The path forward is clear:
- Build a risk-based KYC framework that allocates resources based on actual risk
- Invest in technology and automation to scale compliance efficiently
- Foster a compliance culture across your organization
- Stay current on regulatory changes and adapt proactively, not reactively
- Measure, monitor, and continuously improve your KYC processes
The competitive advantage belongs to those who view KYC not as a cost center to minimize, but as a strategic capability that enables trust, reduces risk, and accelerates growth.
Your KYC program is working when customers don’t notice it – when onboarding is seamless, approvals are instant for low-risk customers, and bad actors are caught early. That’s the goal. That’s the future.
Key Takeaways
- KYC is the foundation of modern financial crime prevention, combining identity verification, risk assessment, and ongoing monitoring
- The 5-step process (CIP → CDD → EDD → Continuous Monitoring → Record-Keeping) is mandated globally with regional variations
- Risk-based KYC dramatically improves both compliance effectiveness and customer experience by tailoring processes to actual risk
- Modern technology can reduce KYC processing time by 80%, from weeks to hours, while improving detection accuracy
- False positives remain a major challenge; AI-powered systems are reaching 97% accuracy, reducing noise by 90%+
- Global regulatory trends emphasize Ultimate Beneficial Ownership transparency, AI accountability, and real-time compliance
- Successful KYC programs view compliance as a competitive advantage, not a cost center